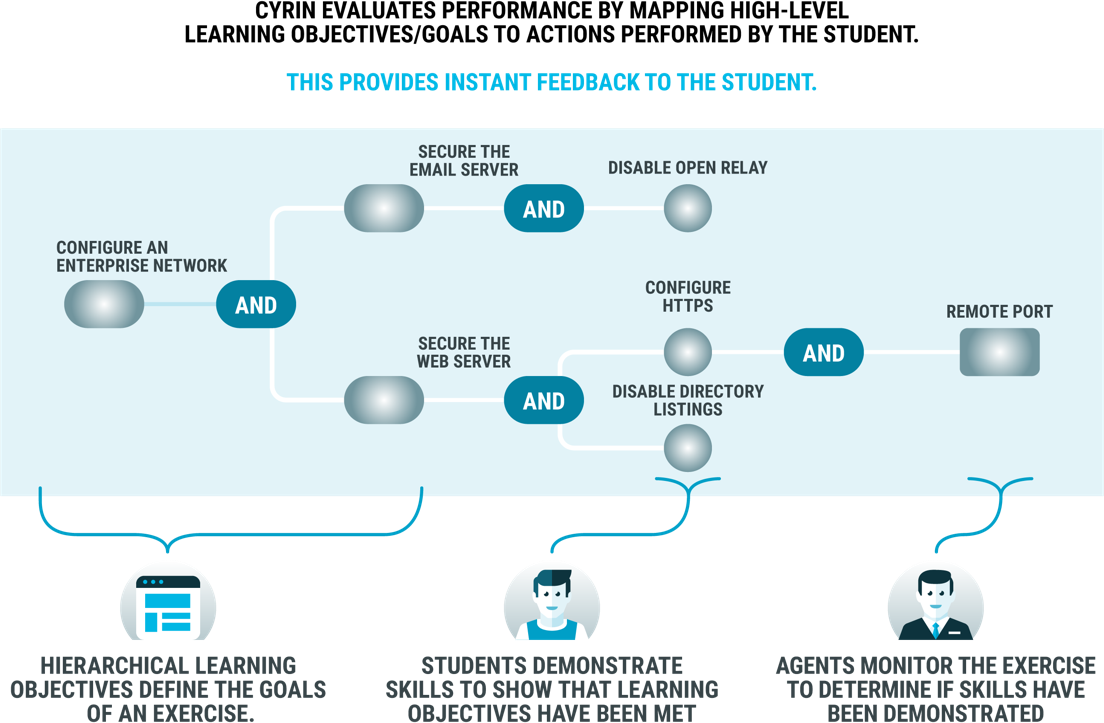
Automatically-created CYRIN exercise in development.

CYRIN Is Different From Other Cyber Ranges.
Real Attacks. Real Tools. Real Scenarios.
Schedule a Demonstration
CYRIN is Engineered to Provide Superior Training in Three Ways
When it comes to cybersecurity for your organization, you have two choices: invest in training now or pay the price later.
ATCorp’s CYRIN® eLearning platform is a simple to use web-based training system that has provided comprehensive training to people in charge of the most sensitive networks in the world — America’s military and first responders.
Unlike other platforms, CYRIN is engineered to provide superior training and education in three ways:
1. Independent High Fidelity Training
Among the innovations built into the CYRIN platform are live exercises where students learn by doing.
Put your employees and students into an attacker’s mind by pitting teams against one another, launching and defending against a variety of realistic attacks. Help them build technical experience with exercises such as setting up web proxies, performing active scans, and discovering server vulnerabilities.

2. Training Flexibility & Exercise Builder: New Labs in Minutes, not Months
Unlike other training systems, CYRIN has a patented Exercise Builder module that allows for fast and easy creation of customized exercises. Exercise Builder allows for real-time modifications and updates that allow you to create labs and exercises to meet your specific training and system needs. CYRIN also easily integrates into an existing cyber range cloud service infrastructure or physical hardware set-up.
3. Comprehensive Student Monitoring
Progress is evaluated in real-time instead of conventional post-training evaluations and can be managed by your company’s CIO, CSO, or Head of IT. Educators love its real-world fidelity and automated student progress metrics. See where your students stumble in real-world scenarios, so you know exactly where more training is required. We call this Automated Performance Monitoring.

Everything CYRIN Cyber Range in Two Minutes
CYRIN is a next-generation cyber range where you train with real tools, real attacks, and real scenarios to hone your skills in a virtual environment. ATCorp's CYRIN Cyber Range provides an active and effective hands-on training environment with virtualized instances of labs, tools, exercises, and attacks.
Watch the video and learn why leading educational institutions and companies in the U.S. have adopted the CYRIN system.
Sign-Up, Sign-In, Take a Test Drive.

Looking to try out CYRIN Training®? Our Web Application Security Analysis with OWASP-ZAP lab is available FREE for 30 days. No credit card required!
Try It FreeExplore CYRIN Solutions by Industry
Current Labs, Exercises, and Attack Scenarios
CYRIN currently offers 50+ labs, exercises, and attacks covering a wide variety of IT-related and cyber security topics, with a number of additional scenarios in development.
Incident Response
You’ve been hacked, or you only suspect you’ve been hacked. Now what?
View This CategoryNetwork Monitoring and Recon
Once your network is set up securely, you must continue to be vigilant.
View This CategoryVulnerability Scanning
As an IT administrator, it’s important to be aware of the tools potential adversaries are likely to use against your networks and your applications.
View This CategoryWeb Application Security
Web-based applications are the most significant security exposure your organization faces.
View This CategorySecure Network Setup
Setting up your network securely is the first step in preventing attacks and misuse of your resources.
View This CategorySecure System Setup
Defense-in-depth requires individual network hosts to be set up securely, whether they be individual workstations, server systems, or cloud computing nodes.
View This CategorySecure Web Application Setup
Securely configuring web server software and frameworks is the foundation of creating secure web-based services.
View This CategoryIndustrial Control Systems/SCADA
Gain insight that addresses trends, challenges, and best practices for defending Industrial Control Systems and SCADA networks.
View This CategoryAttack, Defense, and Incident Response Scenarios
Test your abilities with virtual capture-the-flag, defacement, forensics, and denial of service scenarios.
View This CategoryWhy Choose CYRIN?
Real Tools, Real Attacks, Real Scenarios.
CYRIN sets a new standard for cybersecurity training, innovation, and design. Quick to set up and administer, low cost and user-friendly CYRIN has been engineered to challenge and sharpen the skills of even the most experienced IT professionals.
Make sure your first experience with a cyber-attack isn’t against mission-critical systems. Be proactive in the fight to maintain the integrity of information systems. Choose the best, choose CYRIN.
Contact Architecture Technology Corporation to learn more.

Contact us for a personalized demo, a FREE 30-day test-drive of the CYRIN Cyber Range, or more information
Call +1-800-850-2170, e-mail us at info@cyrintraining.com, or submit the form below.
ARCHITECTURE TECHNOLOGY CORPORATION (ATCorp) is where talented individuals in R&D and engineering create and design real world systems. ATCorp’s core technical areas are next-gen networking, cybersecurity, airspace traffic modeling, high-performance computing, information management, and engineering for complex hardware/software systems.